With AIs coming into our day-to-day life and tonnes of our data floating online. Security is the most crucial element for any software, application, or new technology being launched to users today. To stay ahead of the cyber attacks many practices have been implemented so far by developers & firms. In fact, in 2021, the rise in cybercrime from various sources cost the world more than USD 6 trillion. That’s a lot!
To avoid spending heavy amounts on numerous security measures, DevSecOps- a new approach involving collaboration of Development, Security, and Operations has emerged as an ultimate protector for software development companies.
Based on recent DevSecOps statistics, 36% of respondents currently develop software using DevSecOps, as opposed to only 27% in 2020. Additionally, companies that have adopted DevSecOps reported a 50% reduction in vulnerabilities and a 30% faster time to market. Isn’t that cool? Worry not you can do it too!
In this blog you get a beginner’s handbook on DevSecOps, exploring the definition, key differences between DevOps & DevSecOps , its workflow model, tools, best practices, benefits, and challenges that organizations can learn to improve their security posture and slay in app development. Without any extra fuss, let’s begin.
Overview: DevSecOps
DevSecOps as the name says- is a combination of Development, Security, and Operations. Through this approach, security practices are implemented within the DevOps process. But, if you are unaware of DevOps; then you can explore our detailed guides on DevOps first.
DevSecOps is responsible for an incredible collaboration between development, operations, and security teams to deliver software applications. These apps are rich in security, with major vulnerabilities removed, and risks minimized.
DevSecOps encourages the “shift left” concept, for its phenomenal secure process. This concept suggests that security measures are incorporated at the earliest stages of development, instead of testing and addressing them later.
Difference: DevOps vs DevSecOps
DevOps is defined majorly as the collaboration of development and operations teams. However, it is not just limited to that! DevOps is a spectacular approach that not only combines development and IT operations for the software development lifecycle but also involves automation, continuous integration, and deployment at much faster speeds as compared to traditional development.
Still, to acquire the maximum advantage of agility and responsiveness of a DevOps approach, IT security plays a vital role in the complete life cycle of the applications.
This security concern is extended further in the form of the DevSecOps approach. DevSecOps involves incorporating security practices and measures into the development process at an earlier stage. On a side where DevOps focuses majorly on speed and efficiency, DevSecOps focuses on building secure applications from the initial stages of development.
Previously, the role of security in DevOps was limited to the final stages. It was appropriate then because the development cycles lasted merely for months or even years. But now effective DevOps offers rapid and frequent development cycles that are sometimes weeks or days long. Any smart person can conclude that an outdated security practice can undo even the most efficient DevOps initiatives. That’s how DevSecOps gets its throne firm at the table of modern security services.

How does DevSecOps model work?
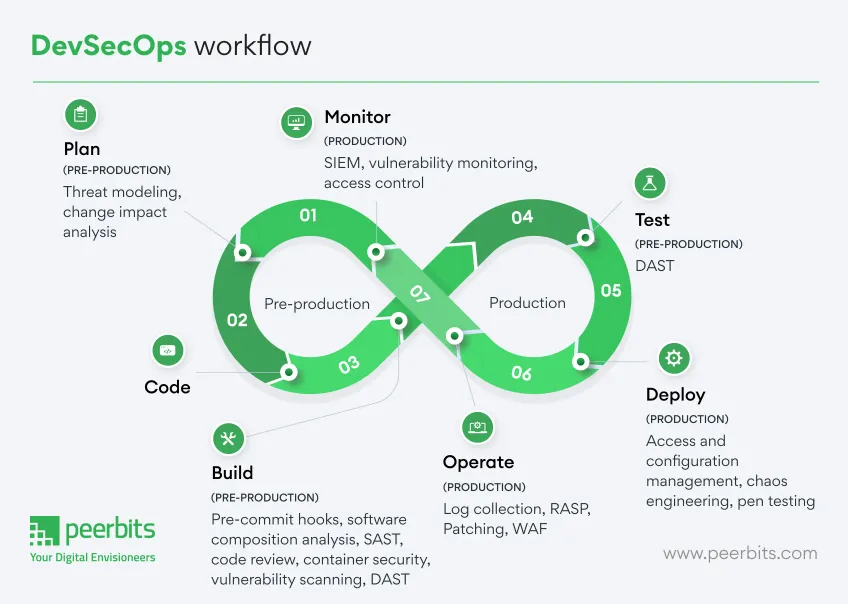
The functionality of DevSecOps model involves integrating security practices within the DevOps workflow. It makes sure that security is addressed at every stage of the software development lifecycle. Here are some significant stages of DevSecOps pipeline:
-
Plan: At this stage developers, operations, and business leaders come together to strategize, identify requirements, set goals, and set the scope of the project.
-
Code: At this stage, developers write, review, and version-control source code of the security best practises following the coding standards and guidelines.
-
Build: Further, in build stage of DevSecOps the source code is compiled, and dependencies are finalised to create a build artifact, such as a binary or a container image.
-
Test: At this stage, the previously build artifact is put to various tests, including unit, integration, performance, and user acceptance testing. This stage confirms the functionality, performance, and reliability of the DevSecOps approach.
-
Deploy: Once the build artifact passes all tests, it is then deployed to production, utilizing automated deployment tools and continuous delivery pipelines.
-
Operate: The work is not finished on deployment! As the deployed application is monitored for performance, reliability, and availability to ensure a resistant lifecycle.
-
Monitor: This stage is where continuous monitoring of the application, infrastructure, and user feedback happens. It is highly necessary to identify areas for improvement and plan future iterations based on present insights.
Apart from all these usual stages, DevSecOps brings security hardening at each stage of the DevOps workflow as follows:
-
Infrastructure hardening: It refers to integrating security best practices into the underlying infrastructure and configuration management. Some of the popular practices include- applying the principle of least privilege, using secure network architectures, rest and in transit data encryption, regular patching, and implementing secure access controls. Many even use Infrastructure as Code (IaC) tools to automate and implement security configurations.
-
Pipeline hardening: In this phase of DevSecOps, security is added to the CI/CD pipeline.This makes sure that security checks and tests are run at every stage. It involves static and dynamic application security testing (SAST and DAST), container security scanning, vulnerability assessment, and dependency analysis.
-
Application hardening: This stage includes, embedding security in the application development process with developers following the best practices & guidelines. Through, regular code reviews and automated security testing, issues are detected early in the development process.
Automation in DevSecOps: The ultimate feature
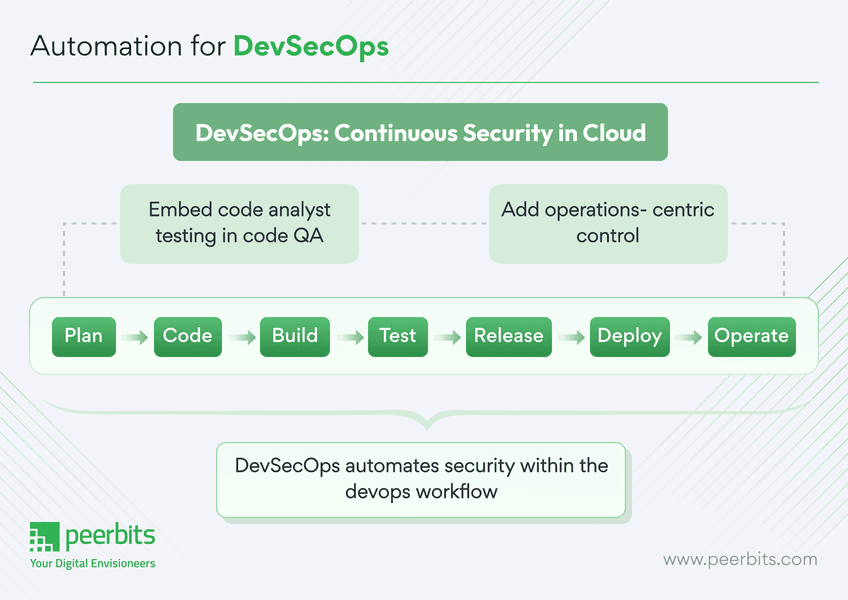
Automation is the core of DevSecOps, which becomes a resilient force for a variety of development and security teams.
Automation in DevSecOps powers up the deployment pipeline, reduces manual errors, and enforces consistent security controls throughout the development lifecycle. DevSecOps and automation are the two flag-holders of the secure software development process.
DevOps automation with this new approach can easily help you improve the efficiency and effectiveness of security checks and scans. Along with that, these efforts are not handled manually due to automation giving much more ease to the developers, encouraging their code quality & innovation practises.
Though, apart from automation, DevSecOps also upholds a variety of tools that help its developers in creation like a child on a stroller. Let’s give it a look!
DevSecOps tools for application security
DevSecOps and security tools are a bulk of life-saver ninjas that help you in integrating security best practices within the DevOps pipeline, automating security tasks, and helping collaborate amongst development, security, and operations teams.
Some of the main categories of DevSecOps tools that you should know are as follows:
- Infrastructure as Code (IaC) tools: IaC tools are responsible for the management and provisioning of computing infrastructure through machine-readable definition files. They help in automating the DevSecOps process of setting up, changing, and versioning infrastructure. This makes implementing security more error-free and consistent.
Eg. Terraform, Ansible, Chef, CloudFormation, etc.
- Static Application Security Testing aka SAST: SAST tools analyze source code, bytecode, or binary code at rest in the infrastructure. They help in identifying potential security vulnerabilities of the apps. These tools help developers detect and fix security issues early in the development process.
Eg. SonarQube, Checkmarx, Veracode, Bandit, etc.
- Dynamic Application Security Testing aka DAST: Just opposite to the SAST, DAST tools are useful in analyzing applications during runtime (explains the terms dynamic after all). It protects your apps from external attacks and identifies potential security weaknesses that can be handled, once the app reaches the production stage.
Eg. Burp Suite, Veracode Dynamic Analysis, HCL AppScan, OWASP ZAP, etc.
- Container security: This is an important DevSecOps tool category, that focuses on securing containerized applications. With the help of these container security tools, users can easily scan container images for issues, manage container deployments, monitor runtime activity, and offer visibility and control over network communications.
Eg. Anchore, Clair, Twistlock, Aqua Security, etc.
- Container networking: These tools for DevSecOps manage and secure the network communications between containers in a microservices architecture. With features like network segmentation, load balancing, and service discovery, container networking tools help in managing inter-container communications effectively and securely.
Eg. Flannel, Weave Net, Calico, Cilium, etc.
- Security monitoring and response tools: These tools of DevSecOps hold a lot of resemblance with DevOps' final security testing. These security monitoring tools collect, filter, integrate, and link data to find out any remaining security breach or anomaly escaped from all the above tools(that’s rare though!). Incident response tools provide a systematic approach to handling and managing the final portions of security events or cyber attacks, that are termed as incidents.
Eg. Splunk, Splunk, Alert Logic, Sumo Logic, etc.
The above-described DevSecOps tools play a crucial role in offering a secure and efficient software development lifecycle for a DevSecOps environment.
DevSecOps Best Practices
By far you’ve understood that a seamless integration of DevSecOps is critical for the security & growth of DevOps.
To achieve this harmonious balance, adopt the following DevSecOps best practices for improved performance and heightened security awareness:
1. Automated security testing:
Automated security testing serves as the foundation of DevSecOps. Regular security assessments, including vulnerability scans, penetration testing, and security code reviews, are seamlessly integrated into the development workflow due to DevSecOps services. Automated tools help in detecting issues and prioritize them according to their severity, allowing development teams to swiftly tackle critical concerns.
2. Continuous monitoring and feedback:
DevSecOps places a strong emphasis on the continuous monitoring of applications that are in production. Real-time surveillance aids in recognizing and addressing security threats immediately. This also allows developers for quick responses and mitigation. DevOps teams can utilize SIEM systems and APM tools to obtain comprehensive insights into application performance.
3. Infrastructure as Code (IaC) security:
With the increasing reliance on code for infrastructure management, securing IaC has become vital. By embedding security measures within the infrastructure code, organizations can guarantee uniform security configurations. They can also minimize the chances of misconfigurations that may lead to security breaches.
4. Collaboration and training:
Collaboration among development, security, and operations teams is essential for DevSecOps success. Cultivating a culture of open dialogue and knowledge-sharing is crucial. Furthermore, offering consistent security awareness training for developers is important to help them stay informed about emerging threats and effective mitigation strategies.
5. Immutable infrastructure:
Consider implementing immutable infrastructure practices, where deployed components are regarded as temporary assets. When problems are identified, the entire component can be replaced with an updated version. This method decreases the attack surface and streamlines the process of patch management for DevSecOps.
Benefits of DevSecOps
DevSecOps can improve the overall security of software with benefits such as:
- Increased security:
By incorporating security into the DevOps workflow, DevSecOps can assist in preventing security vulnerabilities from being introduced into production environments.
- Reduced risk:
Minimize the likelihood of security incidents and data breaches.
- Improved compliance:
Automate procedures that support adherence to security regulations.
- Improved efficiency:
Enhance the software development process's efficiency through automated security checks and scans with DevSecOps practices.
- Improved compliance:
Assist organizations in meeting security regulation requirements.
- Increased collaboration:
Enhance teamwork among development, operations, and security teams by fostering a shared sense of accountability.
- Faster time to market:
Accelerate the software development timeline by automating security checks and scans.
- Improved quality:
Boost software quality by identifying security vulnerabilities early in the development cycle.
- Improved risk management:
Enable organizations to more effectively recognize and manage security risks.
- Increased customer satisfaction:
Enhance customer satisfaction by providing secure and dependable software.
- Reduced costs:
Lower the expenses associated with security incidents and data breaches.
- Improved visibility:
Help organizations achieve greater insight into their security posture, allowing for the swift identification and resolution of security risks.
Challenges in adopting DevSecOps
Organizations may encounter difficulties when first adopting DevSecOps, as it is still an evolving & modern technology. Here are some of the following challenges that firms can encounter while switching to DevSecOps:
-
Diverse technologies: Software development encompasses a variety of technologies, such as different frameworks, programming languages, and architectures, each with its own operational characteristics. This diversity can hinder security teams from effectively testing and monitoring these technologies at the necessary pace.
-
Brittle pipelines: Merging development tools with poorly configured security testing systems can result in fragile pipelines. These fragile pipelines are susceptible to failure if any component malfunctions or automation processes fail.
-
Complex event management: If security teams do not effectively handle triggered events and the associated policies—which can be intricate and labor-intensive—pipeline breakdowns are likely.
-
Risk introduction: Security risks can arise at any stage of the development pipeline. Therefore, it is crucial to implement security checks throughout the software development lifecycle to identify new vulnerabilities as early as possible.
-
Coordination difficulties: Teams may struggle to organize and manage the numerous security checks needed, largely due to the complexities mentioned above, along with challenges related to visibility and prioritization stemming from decentralized development and the unique characteristics of DevSecOps.
Why choose Peerbits for DevSecOps & DevOps services?
DevOps in itself is a highly revolutionary technology that companies nowadays are adopting at an enormous level. Peerbits makes sure to satiate all your modern-day technology needs with our DevOps services.
DevSecOps is offered as part of our DevOps consulting service, where we discuss, plan, strategize, and analyze your requirements. We empower you with effective strategies for ultimate security and best practices. We offer your development teams all essential guidelines for the implementation of DevSecOps, including:
-
Assistance for automated and standardized CI/CD pipelines
-
Extensive compatibility with DevOps tools and platforms
-
Seamless integration with current environments
-
Contextual AI for precise threat detection with reduced false positive rates
-
Emphasis on threat prevention to lessen security impacts and associated costs
Get your hands on the top DevSecOps strategies with our incredible DevOps services. To understand more about such modern technology check our guide to cloud & DevOps solutions from our nerdy blogs.
Conclusion
As development teams refine their processes and adopt new tools, it is essential for them to remain updated about security. DevSecOps is an ongoing process that should be consistently revisited and implemented with each new code release. Threats and attackers continuously upgrade their attacks so why not your protection practices? You can shorten this hassle of finding the best security measures for applications every day and enhance your DevSecOps practices by registering for a free demo today with us.
A great starting point for DevSecOps testing is to automate your testing and ping us; Peerbits- your reliable DevOps solution provider for regular monitoring & assessment. Don’t forget to take a peek at our services of CI/CD pipeline, automation, microservice, and serverless architecture for an ultimate solution.