Most cloud-native businesses aren’t managing just one environment. They’re running dozens — sometimes hundreds across regions, accounts, and stacks. Things break. Logs flood in. Patches are missed. Teams drown in click-ops. It’s here when your business gets haywire and things go out of place.
Maybe this is why we see a jump in cloud usage. In 2025, public cloud spending is expected to cross $700 billion. Meanwhile, 89% of companies are already juggling multi-cloud setups. That’s not slowing down.
And why not!
Traditional ways of managing infrastructure just can’t keep up. There's too much noise, too many alerts, and not nearly enough hands to handle them all.
And this is exactly where AWS Managed Services Automation becomes the game-changer. An incredibly powerful tool that leans on native AWS tools to handle everything from patching to cost optimization in real-time, with no hand holding.
It gives operations, architects, and AWS FinOps Automation teams something they’ve desperately needed: Breathing room.
The outcome?
A reliable, secure, self-aware system that learns and adjusts. AWS automation will provide you with a toolkit that plugs into your workflows and does all the heavy lifting.
So, what exactly does AWS Managed Services Automation bring to the table?
Let’s break that down.
Automation in AWS Managed Services
AWS Managed Services handles the major work that goes into managing your AWS infrastructure. It acts as a service layer that is built to automate, standardize, and harden day-to-day operations without draining your team.
Let’s unpack this with real substance.
Managed services scope
AWS Managed Services isn’t just about running stuff. It’s about redefining the shared responsibility model and giving your team more time to focus on what really matters.
-
Shared‑responsibility shift
Shared-responsibility of AWS Managed Services shifts operational burden on to other services providers. Be it updates, patch cycles, monitoring onto the service provider — your team can step back from infrastructure micromanagement and focus on app-level concerns.
-
24×7 Ops
The 24x7 availability of AWS Managed Services Provider assures round-the-clock monitoring, ticket triage, and automation-first remediation. It means the issues are flagged and fixed before users notice.
-
Patching
Forget spreadsheets and weekly patch windows. Instead, AWS Systems Manager Automation handles patching cycles based on criticality and maintenance windows, and logs every step for AWS Compliance Automation.
-
Incident response
Auto-detection of anomalies. Playbook-driven triage. Runbooks that kick in without waiting for human input. That’s what incident response looks like with AWS Cloud Operations Automation.
Read more: 7 Key Tips to Choose Right AWS Managed Services Partner
Automation as the Backbone
Making your business stand out in a fiercely competitive environment would mean automation no longer remains optional.
With AWS Managed Services Automation, it’s a foundational design principle built to replace manual intervention with codified, reliable, and repeatable processes.
-
Removes click-ops
Manual ops don’t scale. AWS Managed Services eliminates human intervention from repetitive workflows, slashing toil and improving consistency across environments.
-
Enforces standards
Every change passes through guardrails. Tagging policies, IAM boundaries, encryption rules, and more are enforced automatically — that’s AWS Compliance Automation in action.
-
Enables self-healing
Detect. Diagnose. Fix. Without waiting on humans. AWS Systems Manager Automation links health checks with runbooks that restore services to a known-good state.
Automation layers
AWS Managed Services Automation operates across different functional layers. Each of these layers are designed to manage a specific area of the cloud lifecycle, from provisioning all the way to cost and performance tuning.
-
Provisioning
Launch environments using Infrastructure as Code AWS tools like CloudFormation and CDK. It ensures consistent, repeatable setups that can be version-controlled and scaled easily.
-
Deployment
Deploy applications using AWS CodePipeline Automation and CodeDeploy with support for canary and blue/green strategies to reduce the risk of failure and shorten rollback time.
-
B.3.3 Runtime Ops
Automatically monitor, log, and alert using CloudWatch, EventBridge, and AWS Systems Manager Automation. Operational issues are flagged and acted upon immediately.
-
Optimization
Monitor cost and performance metrics. AWS Compute Optimizer and AWS cost Savings Plans recommend actions that reduce spend while maintaining efficiency.
Application of automation layers in practice
There are different layers where AWS Managed Services Automation contributes. Each plays a specific role in keeping your AWS setup fast, secure, and cost-efficient.
You’ve got provisioning, compliance, deployments, monitoring, security, cost control — and now, AIOps & MLOps to automate critical operational tasks.
Here’s how each layer translates into real action:
| Layer | Key Objectives | Typical AWS Mechanisms |
|---|---|---|
| Provisioning / IaC | Repeatable builds, drift prevention | CloudFormation, CDK |
| Config & Compliance | Enforce baselines | AWS Config rules, Systems Manager State Manager |
| CI/CD & Release | Fast, low‑risk deploys | CodePipeline, CodeDeploy, Blue/Green, Canary |
| Ops & Monitoring | Detect, diagnose, heal | CloudWatch, EventBridge, SSM Automation |
| Security & Risk | Continuous guardrails | Security Hub, GuardDuty, Inspector |
| Cost & FinOps | Auto‑rightsizing, spend controls | Compute Optimizer, Budgets, Savings‑Plans recs |
| AIOps | Anomaly prediction, chat‑ops | DevOps Guru, AWS Q, CodeWhisperer |
Each of these AWS Automation Tools feeds into the next.
For example, provisioning relies on Infrastructure as Code AWS methods like CloudFormation. Deployment flows through CodePipeline with approval gates.
AWS security assessment & automation enables continuous scanning. AWS FinOps Automation tools run in parallel to track spend and trigger rightsizing actions.
That’s the core of the best tools for automating AWS Managed Services — all speaking the same language.
Deep dive into core AWS automation tools
AWS isn’t short on automation tools. But what matters is how you use them and where they fit in your workflows.
Let’s walk through the ones that really do the heavy lifting.
#1. Infrastructure as Code
Infrastructure as Code AWS is where operational automation begins.
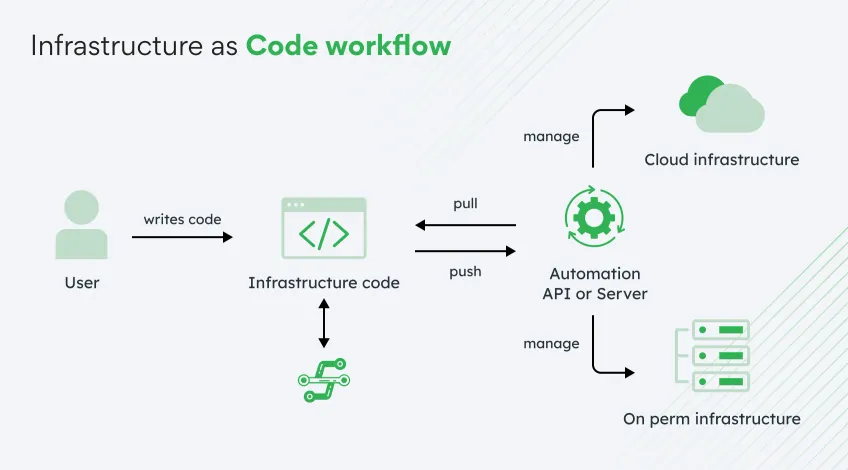
Instead of clicking through the console, teams can define, provision, and maintain infrastructure using code — reducing human error, increasing speed, and enforcing compliance automatically.
-
CloudFormation (stack sets, change sets)
AWS CloudFormation lets you define entire infrastructures in JSON or YAML. StackSets allow deployment across multiple accounts and regions simultaneously.
Change Sets simulate updates before applying them, helping you anticipate the outcome and prevent unexpected breakage — key to safe rollout at scale.
-
AWS CDK & Cloud Control API
AWS CDK lets developers define infrastructure using familiar programming languages like Python or TypeScript. It translates high-level code into CloudFormation templates.
Also, the Cloud Control API offers cross-service resource visibility and lets you detect drifts programmatically — a core part of AWS Compliance Automation.
Read more: How automation with AWS CDK helps in business expansion?
#2. Deployment automation
Deployment automation in AWS Managed Services is all about moving code from repository to runtime with minimal risk and maximum traceability.
-
CodePipeline orchestration
CodePipeline creates end-to-end pipelines that automate every step of the delivery
workflow — source, build, test, and deploy. You define what happens at each stage, with automated triggers, approval gates, and rollback logic for safer shipping.
-
CodeBuild for test automation
Tests should never be an afterthought since AWS Managed Services enable leveraging the CodeBuild.
CodeBuild compiles your code, runs your tests inside isolated containers, and integrates into CodePipeline so every deployment includes a validation layer.
-
CodeDeploy with blue/green & Lambda hooks
To eliminate downtime during releases, CodeDeploy uses blue/green or canary strategies to shift traffic gradually.
Pre- and post-deploy Lambda hooks let you run configuration checks or rollbacks automatically based on outcome.
#3. Operations & patch automation
This is where AWS Systems Manager Automation comes into its own. Whether it’s routine patching or incident resolution, automation replaces repetitive tasks with structured workflows that scale.
-
Systems manager automation runbooks
Runbooks are predefined automation documents that execute multiple steps — like checking status, applying patches, restarting services — all without human intervention. You can run them manually, schedule them, or trigger based on monitoring events.
-
Patch manager
Patch Manager, part of AWS cloud computing services, automates OS-level patching across your fleet. You define patch baselines and maintenance windows, and the system applies updates based on severity or compliance rules. It also integrates with AWS Config to track patch status.
-
OpsCenter ticket enrichment
When incidents occur, they’re routed to OpsCenter with automatic context pulled in — affected resources, logs, CloudTrail data — helping engineers diagnose and resolve faster, or letting automation take over completely.
#4. Event-driven automation
Real-time, event-based actions form the fundamentals of responsive cloud operations. It’s here where the AWS Managed Services drive automation with native triggers and step logic.
-
EventBridge rules
You can create rules to respond to nearly anything — like failed deployments, high CPU, or unauthorized access.
These rules can invoke Lambda, Systems Manager, or even workflows across accounts.
-
Step Functions workflows
For complex automation scenarios — such as rolling restarts or phased updates. For instance, step Functions offer stateful orchestration. You can string together tasks, retries, error handling, and human approvals as needed.
#5. Auto scaling & self-healing
Scalability and resilience don’t happen manually.
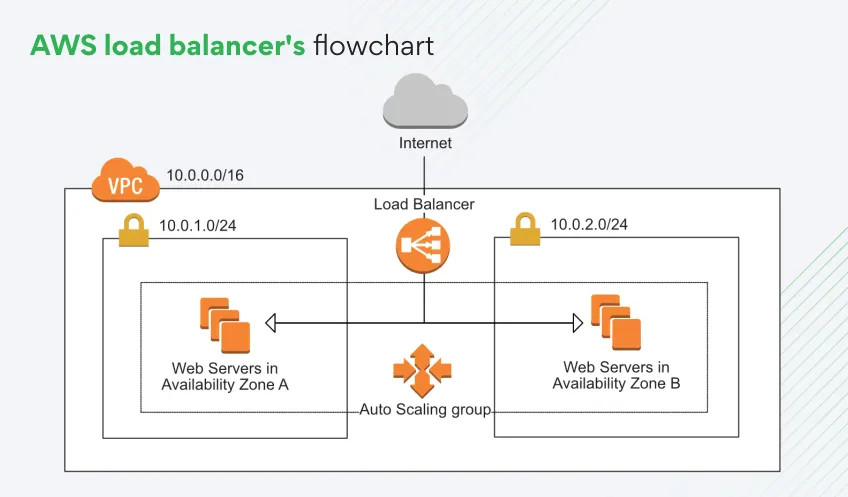
Instead, you can have AWS automation enabling the much-needed predictive logic and dynamic resource management.
-
EC2 Auto scaling groups
ASGs scale compute based on traffic or scheduled needs. Predictive scaling uses historical trends to prepare capacity ahead of spikes, reducing cold starts.
-
Lambda reserved concurrency
By assigning minimum concurrency, you prevent cold starts and ensure predictable response during surges.
-
ECS/EKS capacity providers
Containers can now auto-scale across spot/on-demand nodes. Capacity providers let you define how much should run where — combining performance with cost efficiency.
#6. Security automation
Security automation in AWS is not just about reacting to vulnerability incidents but also staying ahead.
AWS Security Automation tools detect vulnerabilities, enforce guardrails, and launch pre-approved remediation without waiting for human response.
-
Security Hub → EventBridge → SSM
Security Hub aggregates findings across tools.
EventBridge rules detect critical issues and trigger Systems Manager to isolate or remediate, such as quarantining an EC2 instance.
-
Inspector CVE scans
Inspector scans compute instances and containers for known vulnerabilities. It continuously assesses risk and reports exposure in real time.
-
Macie for sensitive data
Macie automatically discovers and classifies sensitive data like PII in S3 buckets. It flags unusual access or exposure so remediation can kick in fast.
#7. Cost optimization automation
Reducing waste is a constant goal. AWS cost-saving tools run in the background to surface inefficiencies and adjust usage accordingly.
-
Compute Optimizer
It analyzes historical usage and recommends optimal instance types. You’ll get sizing guidance for EC2, EBS, Lambda — and even container tasks.
-
Savings Plans recommendations API
This API helps FinOps teams make purchasing decisions. It surfaces patterns and auto-suggests commitment tiers across compute families to help reduce AWS costs with automation.
#8. Generative AI–driven operations
Generative AI in AWS brings a new dimension to automation — transforming static runbooks and dashboards into real-time conversations, auto-suggestions, and contextual actions across cloud operations.
-
AWS Q (chat-ops + code insights)
AWS Q can answer questions, suggest scripts, and even debug issues across AWS services.
It chats with the developers or ops teams inside Slack or console.
-
CodeWhisperer IaC suggestions
When writing infrastructure code, CodeWhisperer provides auto-suggestions — like templates, validation rules, or security flags — tailored to your environment.
-
Bedrock agents for ticket triage
Agents built on Amazon Bedrock can read ticket logs, identify root causes, and either respond or escalate. It turns a static ticket into an actionable conversation.
Read more: Complete guide to build Generative AI applications on AWS
#9. Integrating third-party & open-source automation
Not everything runs on AWS-native tooling — and that’s okay. AWS Managed Services Automation supports hybrid automation stacks.
-
Terraform + CloudFormation imports
You can import Terraform-managed resources into CloudFormation for unified state tracking. Multi-tool IaC support is now smoother than ever.
-
Ansible SSM plugin
Ansible can run via Systems Manager, letting you push configurations and scripts without opening SSH or custom agents.
-
GitOps on EKS (ArgoCD / Flux)
Git-driven deployment is now possible with ArgoCD and Flux inside EKS. Every commit to Git reflects immediately in the cluster state.
-
CI/CD federation (GitHub Actions, Jenkins)
Run pipelines on GitHub or Jenkins with IAM federation and deploy to AWS via OIDC — securely, without static credentials.
Operationalizing automation in AWS Managed Services
It’s one thing to understand the tools. It’s another to embed them into a working system that runs efficiently, scales with demand, and improves over time. This section looks at how AWS Managed Services Automation is applied day-to-day — from setting up automation frameworks to tracking impact with the right metrics.
Automation patterns & best practices
The most effective AWS automation isn’t ad hoc — it follows proven patterns that reduce risk and increase repeatability.
Landing Zone as Code (Control Tower Account Factory)
Start by deploying a secure, multi-account AWS environment through code. AWS Control Tower’s Account Factory lets you automate account provisioning with policies, guardrails, and baseline services already wired in.
Immutable / Blue-Green / Canary deployments
Replace in-place updates with safe AWS automation deployment patterns. These ensure code changes are tested in isolated environments before production. AWS CodeDeploy, Lambda aliases, and routing weights in API Gateway make it work.
Event-driven auto-remediation
When a compliance breach or resource drift is detected, automation kicks in. AWS Config + EventBridge + Systems Manager = remediation workflows triggered without delay.
ChatOps with Amazon Q + Slack/Teams
Bring automation into the tools your team uses daily. AWS Q integrates with messaging platforms to trigger actions, explain logs, or auto-triage incidents — no context switching required.
Patch & vulnerability management with SSM maintenance windows
Define recurring schedules for patching that align with your service uptime goals. SSM applies patches only during the designated window, ensuring security doesn’t disrupt availability.
Continuous compliance using conformance packs & security hub
Maintain real-time visibility into whether your environment meets internal or external controls. These tools bundle rules together and monitor them continuously.
FinOps automation
Combine AWS Compute Optimizer, Budgets, and custom EventBridge rules to automatically alert or even throttle workloads that exceed defined budgets — keeping cost drift in check.
AIOps observability via DevOps Guru
Use machine learning to detect anomalies, noise down alerts, and surface root causes in minutes. AWS DevOps Guru helps ops teams move from reactive to proactive faster.
Read more: Complete guide to AIOps: Automate IT Operations with AI
KPIs & ROI of Automation
No automation strategy is complete without a way to measure its impact. These KPIs give you a complete view across operational efficiency, financial gains, and team productivity.
Operational metrics
Measure the health and agility of your cloud environment. These metrics help assess if automation is actually improving system reliability and release cycles.
- Mean Time to Resolution (MTTR): Automation reduces MTTR by triggering remediations instantly — often before teams even receive alerts.
- Change Failure Rate (CFR): Blue-green and canary patterns, along with automated rollbacks, reduce the blast radius of failed deployments.
- Deployment frequency: Pipelines remove bottlenecks, letting teams release multiple times a day instead of weekly or monthly.
Financial metrics
Track the real money saved or optimized. These indicators show whether your automation efforts reduce waste, avoid overspend, and improve resource efficiency.
- Cost savings from rightsizing & commitments: Compute Optimizer and Savings Plans recommendations directly reduce waste.
- Cost-per-deployment or cost-per-ticket: Fewer manual tickets and safer releases help bring down support costs per unit of change.
Productivity Metrics
Focus on how much manual work is eliminated. These metrics highlight how automation frees up engineers for higher-value work, not just how fast things move.
- Tickets auto-remediated vs. manual: The more auto-closed incidents, the more your automation is maturing.
- Engineer hours reclaimed: Every automated patch, scan, or deploy saves engineering cycles. Track how many tickets never reached a human.
Business impact
Reveal the ripple effects of automation — improved SLAs, shorter feature delivery cycles, and overall customer satisfaction gains. These align tech results with business priorities, reflecting the health of your release pipeline and user-facing service quality.
- SLA/SLO adherence: Fewer outages, tighter response times — SLAs are easier to hit.
- Lead time reduction: From idea to production is shorter when infra and code changes move through automated gates.
Reporting & visualization
Turn automation results into digestible insights. These tools turn scattered data into dashboards and reports that drive better planning and cross-team alignment. gets improved — but only if it’s visible.
- CloudWatch dashboards: Real-time health checks, error spikes, auto-heal events — all in one glance.
- QuickSight FinOps boards: These visualize savings, cost anomalies, and usage patterns in a way that’s accessible even to non-engineers.
- Executive scorecards: Think weekly snapshots that convert automation impact into business metrics — cost avoided, risks prevented, availability maintained.
Implementation roadmap
Knowing what AWS Managed Services Automation can do is one thing — making it work in your environment is another.
This section walks through a realistic step-by-step plan to implement automation, whether you're starting fresh or scaling up an existing setup.
A. Maturity assessment & gap analysis
Begin by evaluating your current state. Where are manual processes slowing you down? Which parts of your infrastructure lack visibility or security automation? A maturity model helps identify gaps across provisioning, monitoring, compliance, cost, and incident response. This step gives you a map of what’s missing.
B. Toolchain selection aligned to automation layers
Based on your cloud assessment, select the right AWS automation tools for each layer — Infrastructure as Code (CloudFormation, CDK), Deployment (CodePipeline, CodeDeploy), Monitoring (CloudWatch), Security (Security Hub, GuardDuty), and FinOps (Budgets, Compute Optimizer). Match each pain point to a tool that solves it.
C. Pilot workload automation
Don’t roll out everything at once. Choose one workload (like a staging environment or non-critical app) and apply IaC, CI/CD, patch automation, and cost monitoring. This is your testing ground — measure impact, document workflows, and refine playbooks here.
D. Scale via landing zone & Center of Excellence (CoE)
Once the pilot succeeds, scale through Control Tower-based landing zones that automate account creation, baseline security, tagging, and guardrails. Establish a CoE that defines automation standards, reusable templates, and onboarding processes for new teams or apps.
E. Continuous improvement with DevOps Guru & FinOps reviews
AWS DevOps Guru helps detect slowdowns and inefficiencies in real time. Combine this with regular FinOps reviews (using QuickSight and Budgets) to optimize for both performance and cost. Feed learnings back into the roadmap for ongoing iteration.
Conclusion
Automation is no longer an option when using AWS. Especially when you’re scaling for modern cloud operations. Be it infrastructure provisioning, patching, deployment, security, cost control, and beyond.
Benefit from AWS Managed Services automation that enables teams to move faster, reduce risk, and focus on innovation. It all goes down to implementing the right tools at the right layers, with a plan that grows alongside your infrastructure.